The Best Tool to Reveal Survivorship Bias is Bug Bounty
/ 4 min read
I regularly speak with security leaders about defense-in-depth and how bug bounty fits in. Recently, it occurred to me just how neatly bounty programs illustrate the concept of survivorship bias, providing a compelling argument for why most organizations should implement one.
The vulnerabilities your bounty program uncovers aren’t random, they’ve survived all your other security controls. Every externally reported bug highlights gaps in your security stack. This is survivorship in action. If your organization is not actively analyzing these outcomes you’re missing a significant opportunity to reduce risk and enhance security processes.
The Bugs You See (and the Ones You Don’t)
While survivorship bias has been widely discussed in tech and information security, its connection to bug bounty remains less explored. Conversations with thousands of organizations have shown me just how substantial this effect can be. In fact, the most mature programs have leveraged this learning method for years.
For the uninitiated, survivorship bias is the tendency to focus on what we can see while ignoring what’s missing. The classic example comes from WWII when statistician Abraham Wald analyzed bullet-riddled airplanes. Initially, engineers reinforced the damaged areas, until they realized the real issue was planes that never returned. The damage they couldn’t see was what truly mattered.1
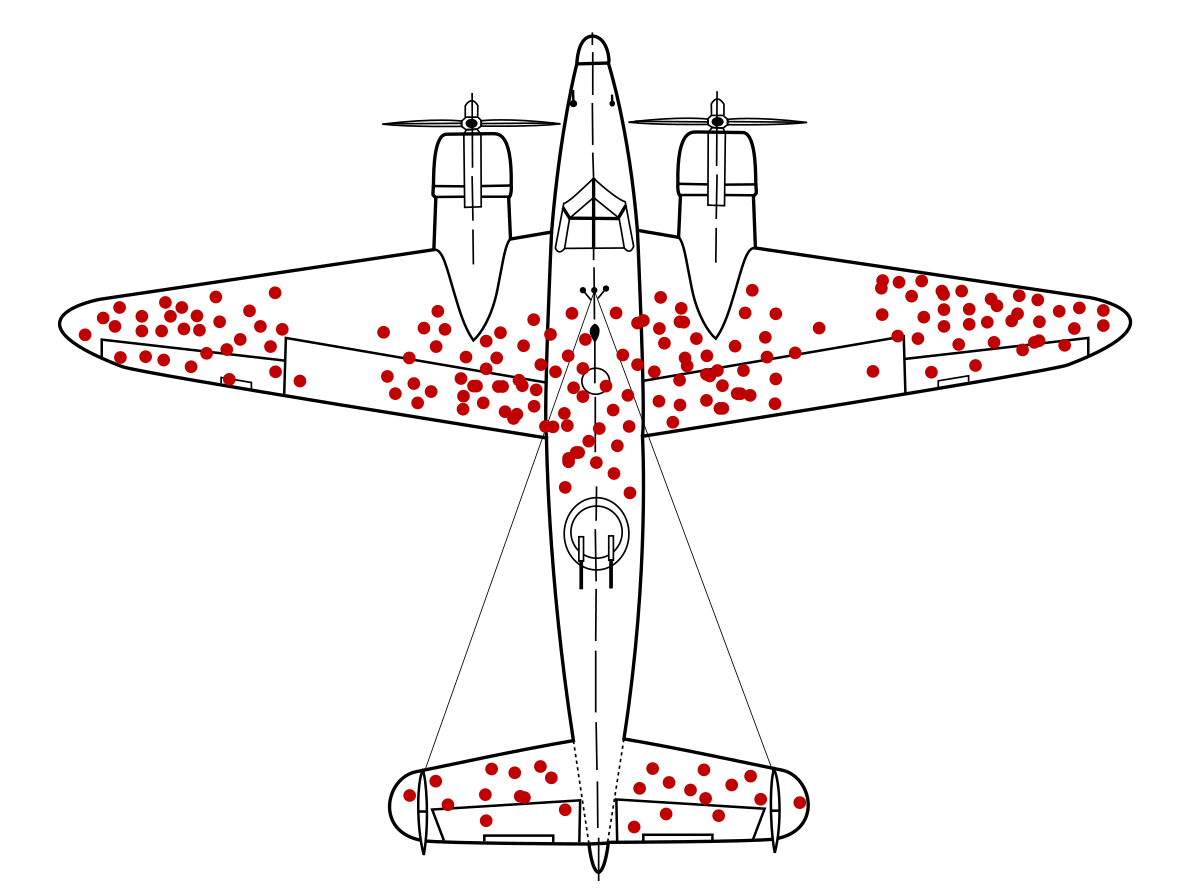 Diagram in which red dots stand for places where surviving planes were shot. Image via Wikipedia.
Diagram in which red dots stand for places where surviving planes were shot. Image via Wikipedia.
Just as WWII engineers initially overlooked critical damage on planes that never returned, security teams may overlook vulnerabilities that don’t trigger existing defenses. If you don’t have a bounty program in place at all, you’re flying blind!
If the Same Bug Keeps Appearing, Look Upstream
A vulnerability that reaches your bounty program bypassed automated security tools, code reviews, threat modeling, penetration testing, and red/blue/purple teaming exercises. Meta/Facebook figured this out a while ago and made a brilliant illustration of this phenomenon:
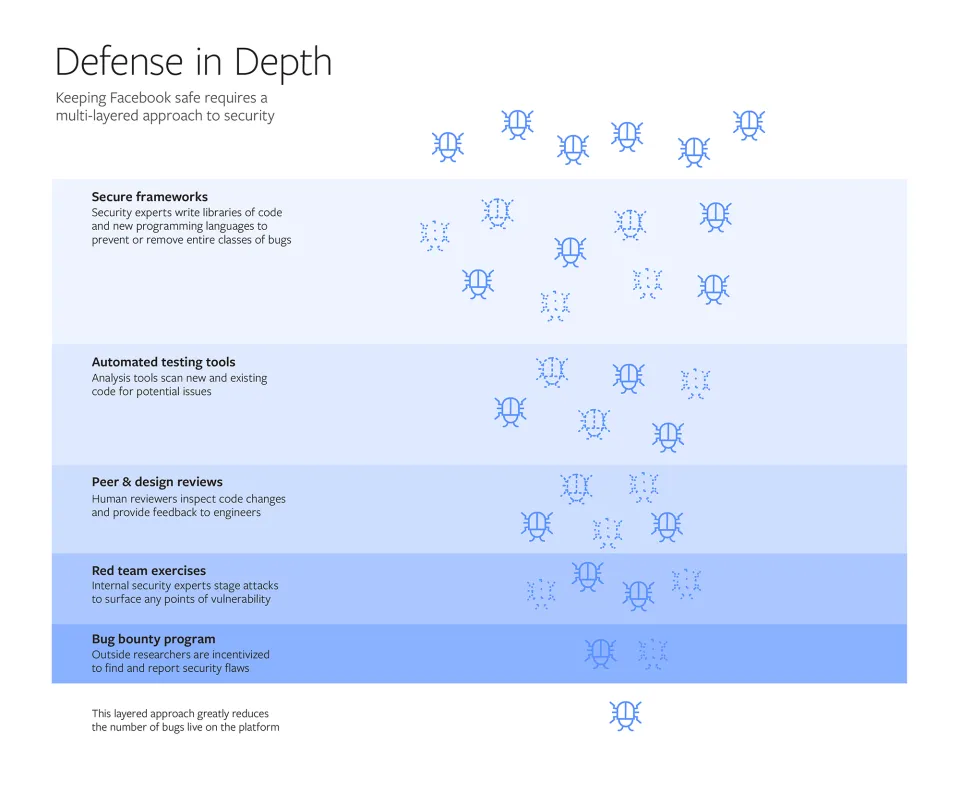 Designing Security for Billions via Meta.
Designing Security for Billions via Meta.
Repeatedly paying for the same type of vulnerability might indicate an upstream issue in a process or tool. Each bounty report should prompt reflection: could this vulnerability have been caught sooner?
- If static or dynamic analysis should’ve detected the issue (XSS, SQL injection, etc.), tuning detection rules may be necessary
- When similar weakness types recur often, turn bug bounty insights into targeted developer training
- Missed OWASP-type issues might call for reconsideration of pentesting scope or methodology
- Persistent design flaws or access control issues might signal deeper security architecture challenges
Without a bug bounty program, organizations lose this valuable feedback loop. They lack clarity about which security measures succeed and which aspects of their security stack fail against real-world testing.
Integrating Survivorship Bias Into Your Security Strategy
It’s simple: start by receiving reports. Launching a bug bounty program doesn’t require immediate public exposure or managing thousands of researchers. Many organizations begin small with private programs, inviting trusted researchers to test under controlled conditions. Others initiate targeted, time-bound engagements, focusing initially on business-critical systems before expanding the scope. You’re probably more ready for this than you think!
Then, measure outcomes effectively. Success isn’t just about finding vulnerabilities; it’s about reducing recurring classes of vulnerabilities over time. Metrics drive internal actions, and bounty payments help quantify the value of security decisions at executive levels.
It’s also worth noting that while some organizations utilize a vulnerability/responsible disclosure programs, these programs rarely deliver comprehensive survivorship insights. Without financial incentives, researchers are less likely to invest significant testing time or effort.2
Don’t Fly Blind
Much like how Wald’s WWII analysis revealed the overlooked vulnerabilities of planes that never returned, bug bounty can do the same for vulnerability discovery and management in your own organization. Bug bounty is not a cure-all (in fact it’s also subject to survivorship bias), but it’s a valuable source of data for any organization. Without such a program it’s easy to overlook crucial opportunities to improve your security tooling and processes.
If you already have a bug bounty program, use it to inform ongoing security improvements, not just as a risk reduction mechanism. If you don’t offer bug bounties already, consider starting a small private program.
The best bug bounty programs don’t just survive, they learn and evolve over time.
Footnotes
-
Bug bounty might actually be the inverse of this example—it’s more like strengthening your air defenses to prevent damage from occurring in the first place! ↩
-
If you don’t have a way to accept vulnerability reports from the public, you should. A VDP is a great way to do this if you aren’t ready a public bounty program. In fact, it’s recommended by NIST! Check out security.txt or HackerOne Essential for free ways to get started. ↩